Data Security and the Evolution Beyond DLP: The Journey Starts Here
Learn how Microsoft Purview can help you protect your data from leaks, breaches, and insider risks with its integrated data security capabilities.
Picture this: a new hire, eager to prove their value but not yet fully versed in corporate protocol, accidentally leaks internal corporate data via email to an external party. Or, a highly-anticipated press release – expected to make waves in your industry – is prematurely revealed before the CEO returns from the business trip where a massive deal was signed. Even more concerning, perhaps you've heard whispers of nation-state-sponsored espionage within your organization, and you're in dire need of robust investigative tools to unmask any suspicious activity… but workers have rights & dignity, you can’t just go snooping around your corporate environment without strong privacy boundaries & transparent security processes.
Sounds like a nightmare, doesn't it? Fortunately, this doesn't have to be your reality. These challenges and more can be effectively addressed with the right data security approach. Enter Microsoft Purview – which has a comprehensive toolset that helps organizations protect sensitive information, prevent data loss, and manage insider risks.
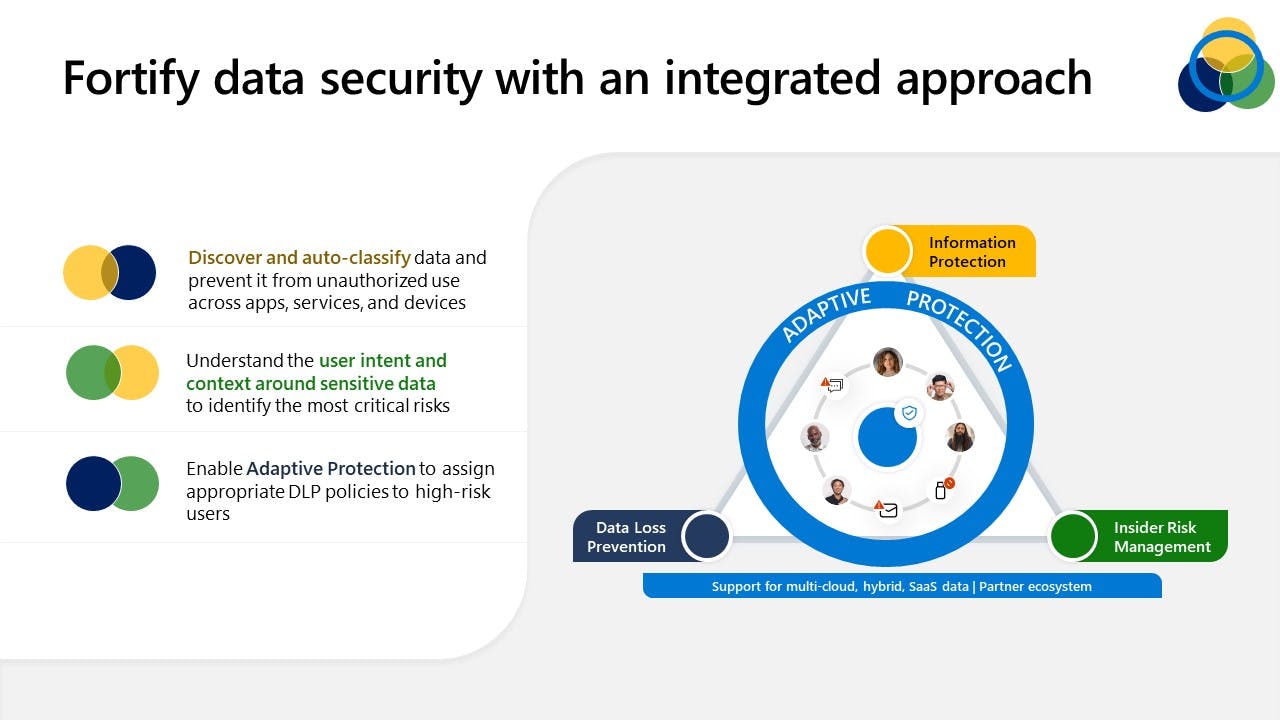
Microsoft Purview offers three main capabilities around data security:
Microsoft Purview Information Protection: It classifies and labels files, ensuring appropriate access and use.
Microsoft Purview Data Loss Prevention (DLP): Designed to stop the unauthorized sharing or downloading of sensitive information based on set criteria, it's your barrier against potential data breaches & leaks.
Microsoft Purview Insider Risk Management: This helps you detect critical data security risks caused by insiders and accelerates time to action in mitigating the risk. For example, if an employee hands in their notice, security controls can dynamically restrict their access to sensitive data like sales contacts or financial reports.
Many organizations jump straight into DLP since DLP solutions have been mature in the enterprise market for over a decade now. But our experience suggests combining it with Information Protection as a foundation could be more beneficial. Why? Because Microsoft's unique approach integrates these two capabilities, providing more robust data protection at the source. This is only the tip of the iceberg.
What's more, Microsoft Purview Information Protection even allows encryption at the file level. This means that even if a document without a DLP policy is shared externally, only those with valid corporate credentials can access it. This is all happening in the background – seamless, secure, and barely noticeable to the end-user to keep him or her productive.
The third cog in the wheel – insider risk management – delivers risk detection for high-risk users, with in-built privacy controls. Unlike most traditional data security approaches, our approach to building insider risk policies is tailored, specific, and respects user privacy.
In the subsequent sections, I'll delve deeper into how the interplay of these capabilities in Microsoft Purview presents a robust defence strategy at the data level, transforming the way businesses manage data security.
Use Case 1: The Curious Case of John Doe: Protecting Private Data in the Age of Digital HR
Imagine John Doe, an enthusiastic new hire in the HR department of a top-tier company. As he settles into his role, he realizes his position is much more than managing employee benefits. His computer contains a goldmine of sensitive information – from bank details for payroll to passport scans for corporate trips.
Here's where things get tricky:
Employee Benefits and Compensation: John might need to email a health insurance provider about a team member's new coverage. Without realizing it, he could be clicking on a fake link sent by cybercriminals. Microsoft Purview DLP can ensure he isn't sending sensitive bank details to fraudulent parties. DLP can detect and block the sending of emails that contain sensitive information such as credit card numbers, bank account details, or payroll information. DLP can also notify John and the security team if he tries to send such information to untrusted recipients or domains.
Travel and Expenses: Organizing a corporate trip? John might need to send passport details to a hotel chain or flight details to a travel agency. He plans to come along during the trip, so he’ll be carrying around his phone and laptop with access to employee health and financial data. Microsoft Purview Information Protection in combination with DLP can help John protect credit card or passport details from malware or spyware that may infect his devices during travel. His company can automatically label and encrypt sensitive files and emails, and apply policies that restrict access, sharing, or printing of those files and emails. Even if somebody else gets hold of the files, they won’t be able to open them.
Training and Development: John is proud of the onboarding progress of a new executive hire and might wish to discuss her potential with external coaches for her development. What if he accidentally shares a file with that executive's salary details instead of her job performance details? Purview DLP can step in here, warning him that the file contains the executive’s personnel ID. John overrides the warning because he knows personnel IDs are linked to both salary and job performance files and he double-checked that this file is a performance spreadsheet, meant to be shared with an executive coach who he knows well.
Why This Matters to You: Every company, large or small, has a John or Jane Doe. In our digital age, a simple click can lead to significant data breaches. On the other hand, John needs to be productive while on the go with his corporate devices and personal or mobile devices, and with these capabilities he’s aware of the right data risks exactly when he needs to be, and company information is protected exactly when it needs to be.
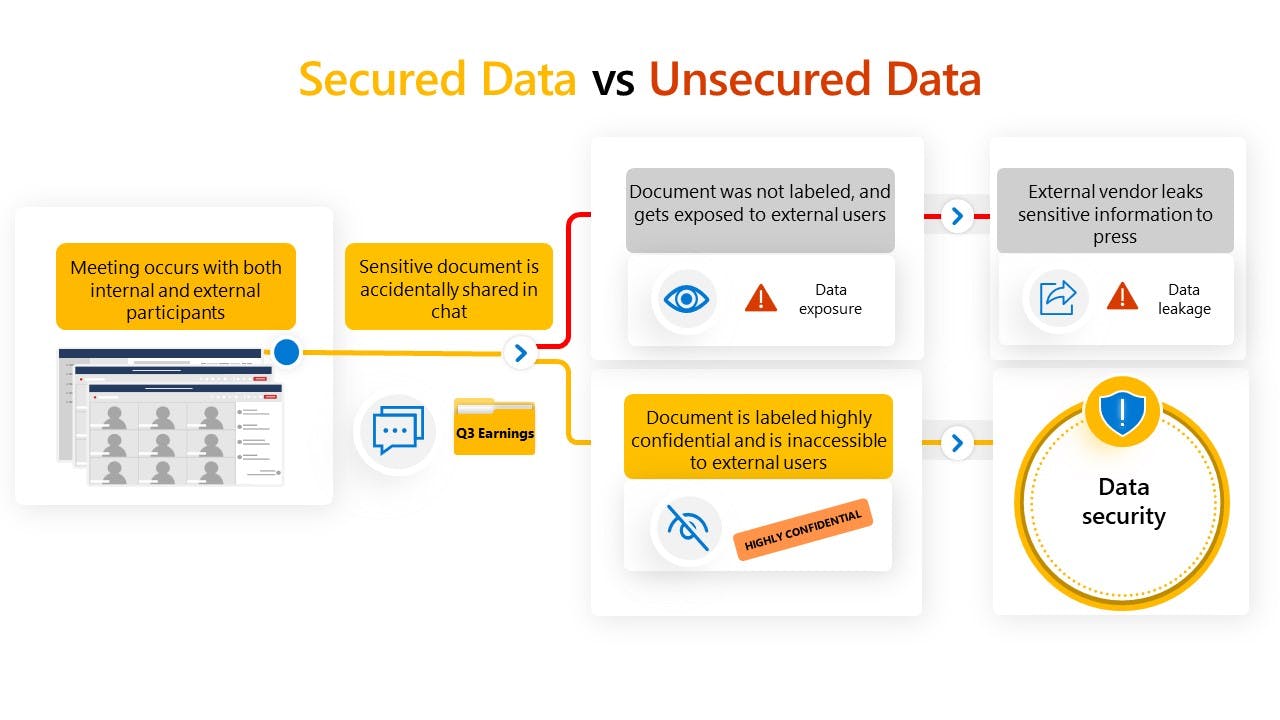
Use Case 2: Securing Big Business Moves in the Digital Age
The executive John onboarded is Abena Sangera. Imagine the weight on her shoulders. Newly appointed as the Chief Executive Officer of a European Fortune 500 company, she's flown from the HQ in the Netherlands to Africa. Her first mission? To finalize a landmark acquisition of a major African unicorn — a deal that promises to catapult her company up the Fortune 500 rankings.
In today's digital world, keeping sensitive business information secure isn't just about hackers on the outside. Sometimes, the real threat comes from within, even if unintentionally. And with the stakes as high as they are for Abena — the trust of her acquisition team, the scrutiny of the global media, and the success of the deal — she can't leave anything to chance.
Setting the Scene: The Pressure of a Groundbreaking Deal
Let’s set the scene: Abena is racing against competitors from Asia and America. She's aware of growing international trade tensions and knows all too well that even a hint of the deal in the media can spin into a geopolitical spectacle. She pictures the potential headlines, the rush of media speculation, and the repercussions it might have on her negotiations.
To counter this, she and her team codename the acquisition 'Project Olivine'. Press releases about the acquisition are prepared, but she insists on a tight lock, ensuring no premature leaks.
Using Advanced Tech to Protect the Deal Documents
Thankfully the security team has already set up the foundational capabilities for data protection in Microsoft Purview Information Protection & Data Loss Prevention.
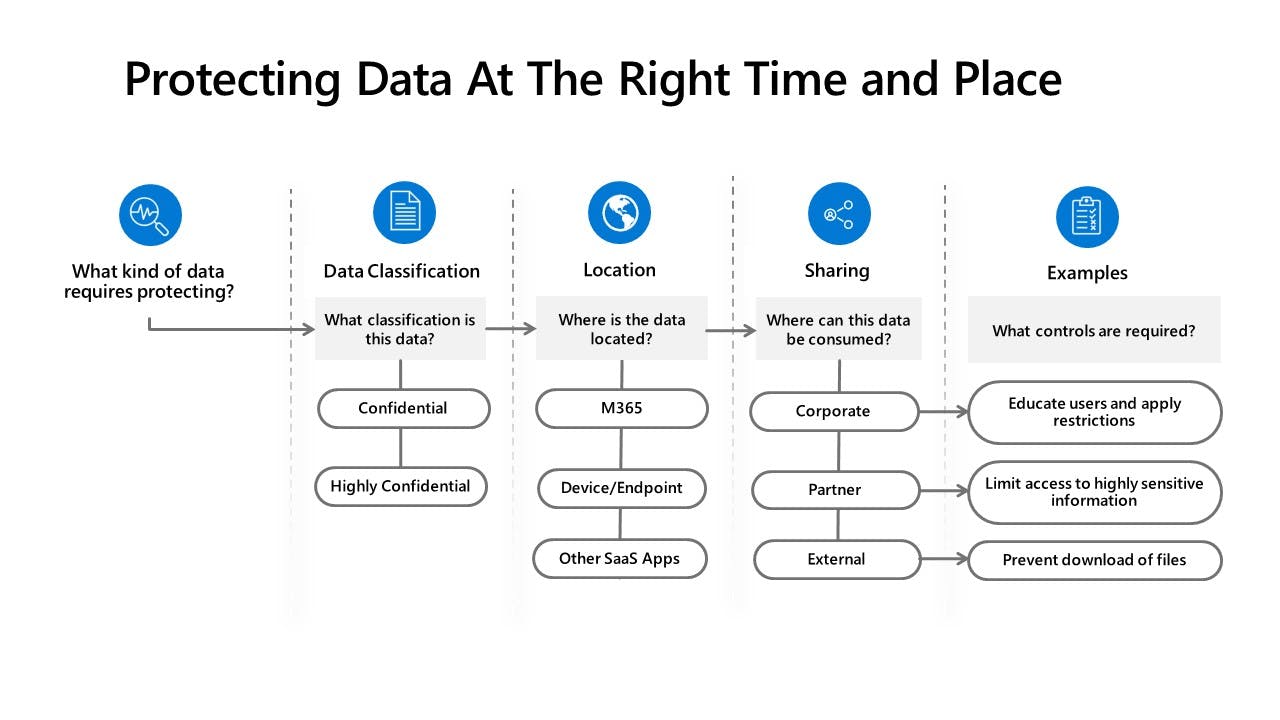
For Abena's acquisition plans the security team needs to take more steps in collaboration with legal & HR. The goal? To quickly detect any leaks related to 'Project Olivine' and to understand not only the “when” and “how” of the leak, but the context behind the leak.
The company prioritizes employee privacy, especially given the strong privacy & labour laws that apply to their European headquarters. They set up a system that only flags high-risk actions on Project Olivine documents, and when such an action occurs, it triggers an Insider Risk alert.
Thanks to just-in-time policy tips, acquisition team members are alerted in realtime when they're performing high-risk actions. If they choose to ignore these alerts and continue with the risky actions, measures are in place. For instance, if a priority team member in the acquisition project downloads an unusually high number of documents for her role on a given day or week, or she has recently handed in her resignation to move to a competitor, this can trigger an Adaptive DLP policy that prevents her from extracting any Project Olivine documents from that point onward.
This ensures that Abena's investigations team can react swiftly to real threats using credible signals.
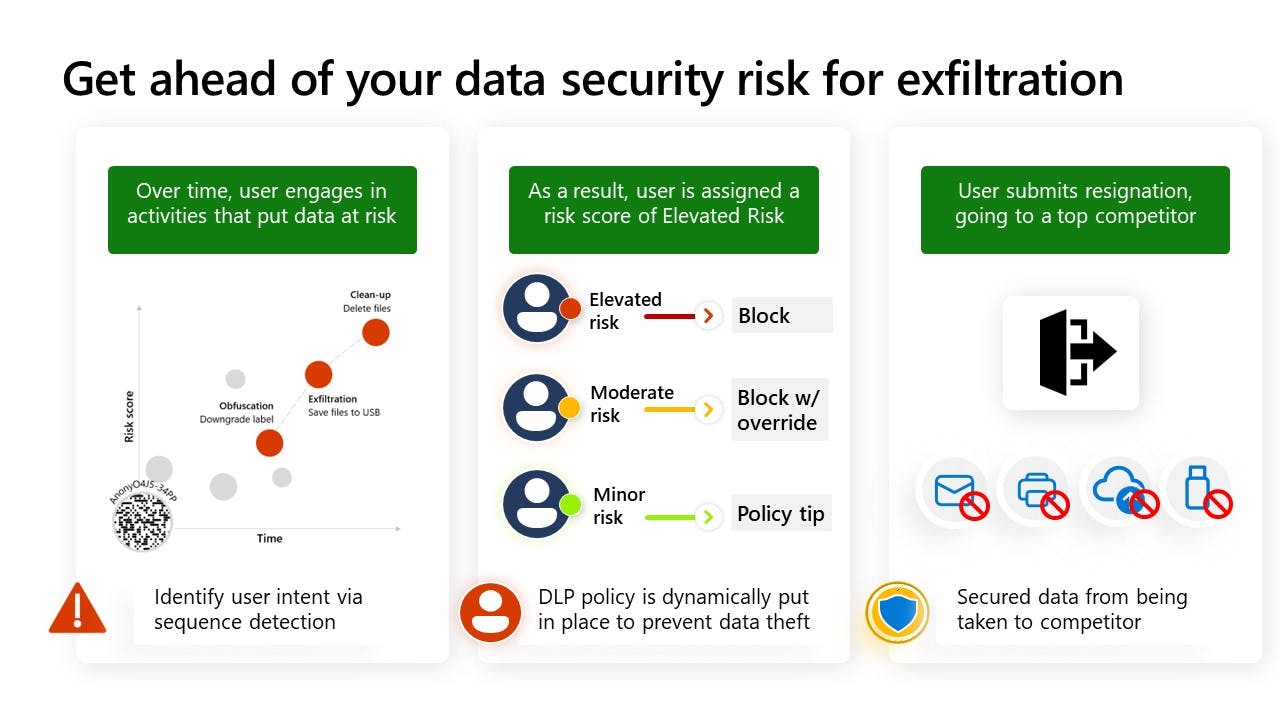
Balancing Security and Employee Rights
It's a balancing act — securing a mega deal while respecting the rights of those involved. By combining data loss prevention and insider risk management, Abena ensures the information related to 'Project Olivine' remains under wraps. And if something does go astray? Authorised security personnel can view alerts generated from pseudonymised users, with the help of sequence detection, and determine whether a high risk leak is intentional or accidental and whether it can damage the deal and justifies closer investigation.
In this interconnected, digital age, it's not just about erecting digital walls. It's about navigating the maze of internal and external threats smartly, ensuring every groundbreaking business move remains secure.
Conclusion: to evolve beyond DLP means building trust in the digital age
As our world becomes increasingly digital and interconnected, the challenges of data security amplify. But, as illustrated with John and Abena's stories, it's not just about prevention and protection. It's about fostering a culture of trust and understanding within organizations. Data security tools like Microsoft Purview’s don't merely act as a digital shield; they become a bridge. They bridge the gap between the necessity of security and respect for individual privacy, enabling businesses to thrive without compromising their employees' rights or the organization's integrity.
Both hypothetical case studies, though different in scope, underscore a universal truth: in today's fast-paced corporate landscape, proactive data security is an enabler, not a constraint. It paves the way for innovation, expansion, and trust-building, allowing enterprises to stay ahead of potential threats while ensuring that their employees can work confidently and productively. As we stand on the cusp of this digital revolution, the question isn't just about how we protect our data, but how we use it responsibly. The evolution of data security has begun, and it promises a future where data isn't just secure, but is also used to empower and inspire.
Thanks to Tina Ying (Product Marketing Manager at Microsoft) for reviewing my blog. All images used in this blog were taken from or inspired by several product and technical teams at Microsoft. Consider the images Microsoft's, but the opinions my own.