Secure File Uploads Guide for Admins: Dropbox, Google Drive, ChatGPT & More
Answering Real-World Questions from Enterprise System Admins
"How do we steer clear of the data leak quicksand that comes with employees using personal software like Dropbox, Google Drive, and ChatGPT, while still keeping corporate data and productivity flowing smoothly?"
Data within personally used web apps (where people use their non-work credentials) cannot be monitored for risk by Microsoft's enterprise security solutions. Nonetheless, employees & contractors still move files and text to those personal spaces for all sorts of reasons. So the question is about how to prevent sensitive corporate data from ever getting there in the first place.
To protect against risk here, you need to onboard corporate desktop devices into the Purview compliance portal. I’ll write on 3 aspects:
What Data Loss Prevention (DLP) looks like
Location to apply a DLP policy to get this to work -> devices
Prerequisites to be able to apply & monitor DLP on corporate devices
a. Method of onboarding devices to the Purview portal
b. Supported browsers where “risky” personal web apps (Dropbox, Google Drive, Personal OneDrive etc.) can be “greylisted”
c. Allowing or blocking web apps in Microsoft Purview’s DLP settings.
Before you start, keep in mind that you're only ready to try this if your org is roughly at the 4th step of its Zero Trust deployment plan with Microsoft 365. Now... let's begin.
1. What Data Loss Prevention (DLP) looks like
When asking this question, admins usually intend to prevent something like an upload of sensitive files to personal storage
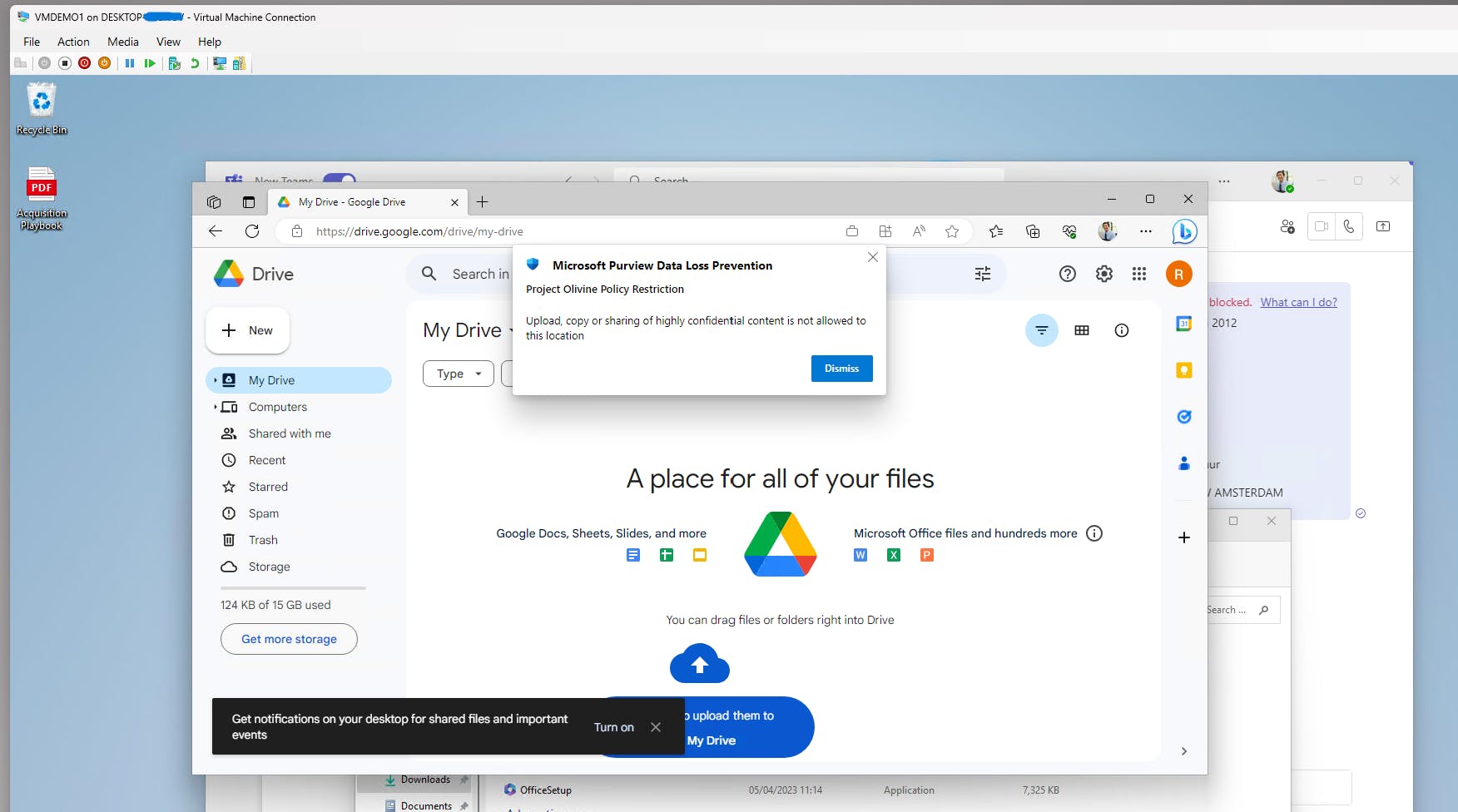
Or prevent copying certain information into a personal gen AI chatbot
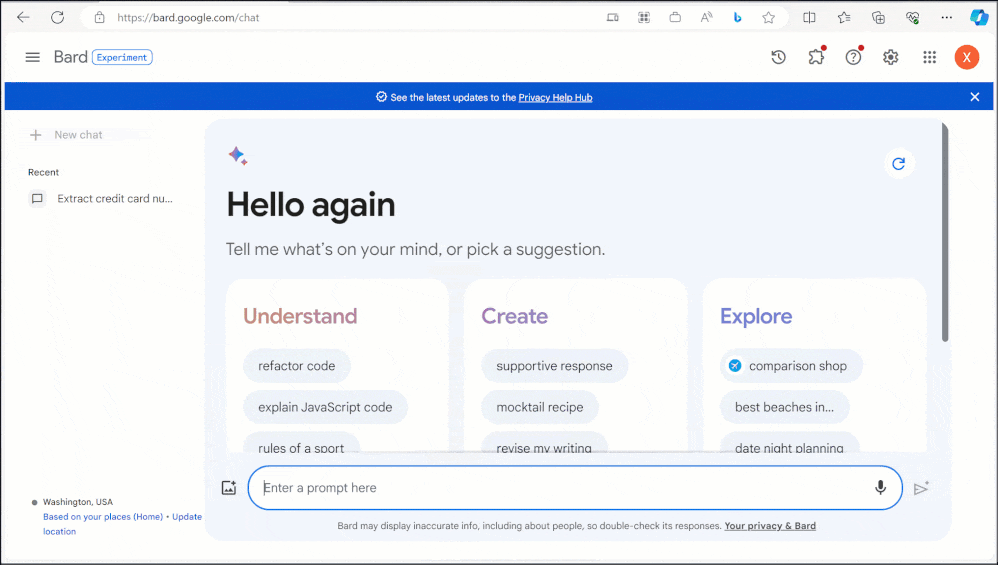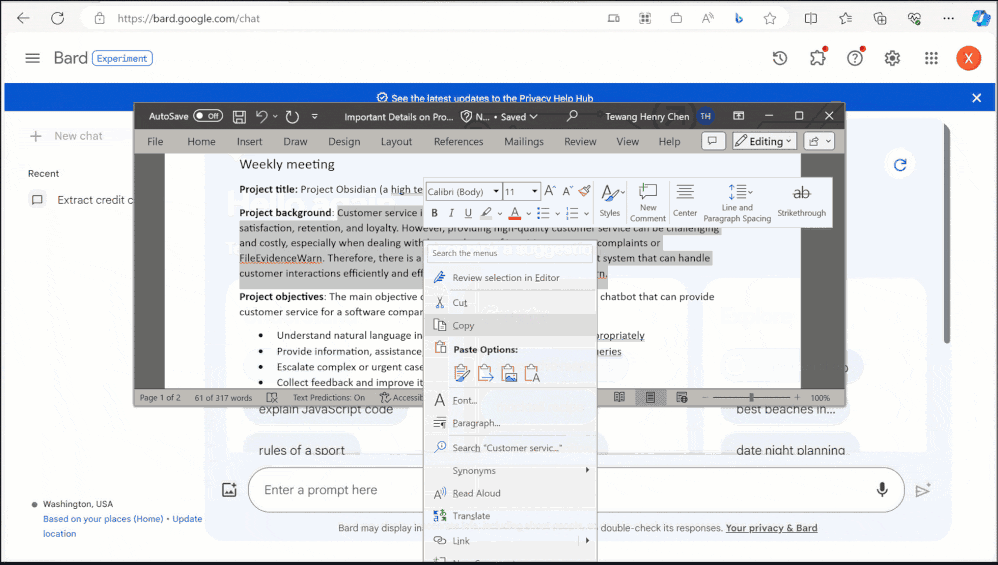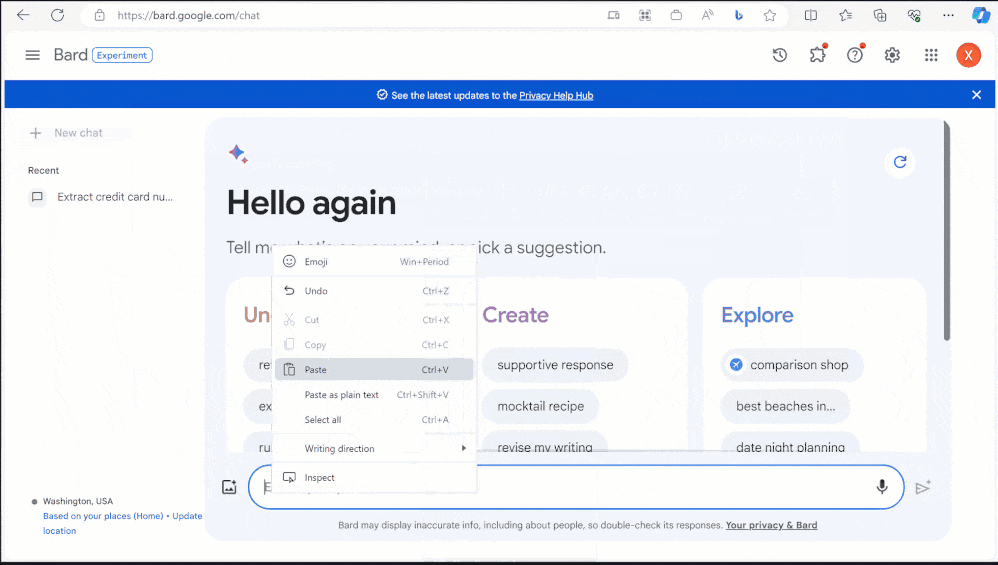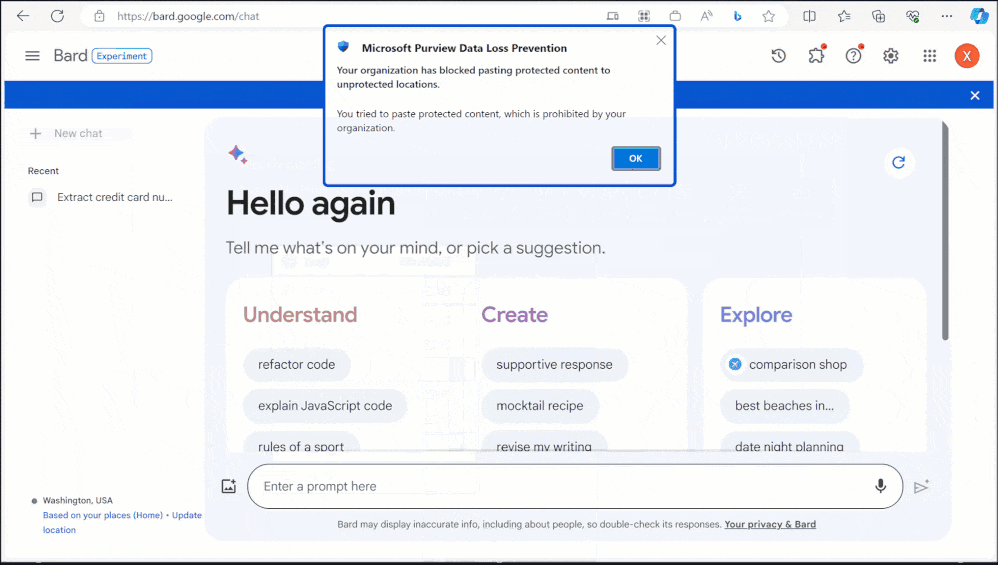
2. Location to apply a DLP policy to get this to work -> devices
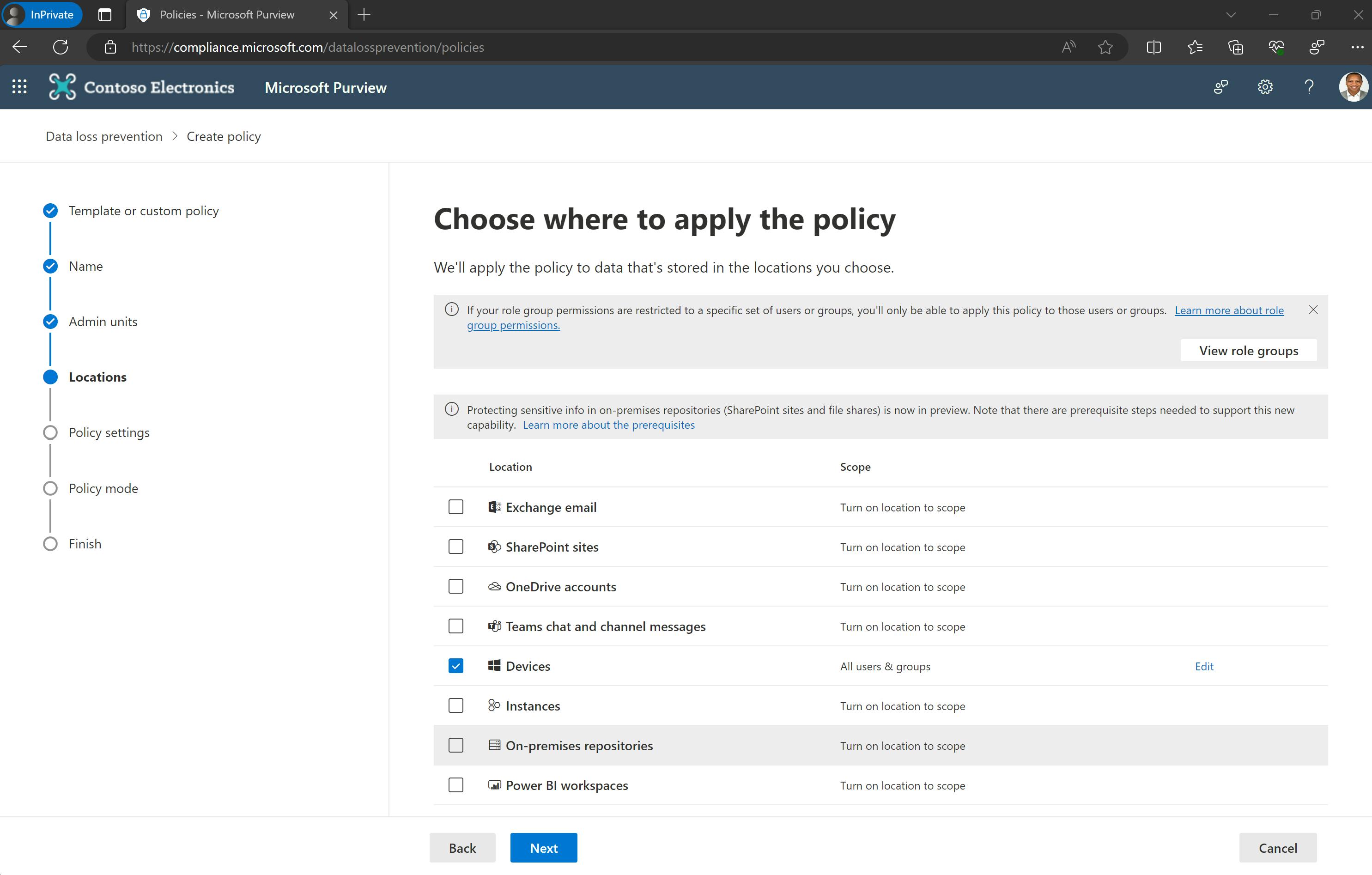
The primary method to block uploads to personally used web apps is to implement endpoint DLP. This prevents the file/text from leaving the corporate device and ever getting to the web app at all. See "Devices" below selected as a location in a DLP policy.
3. Prerequisites to be able to apply & monitor DLP on corporate devices
There are some prerequisites you need to have for this to work.
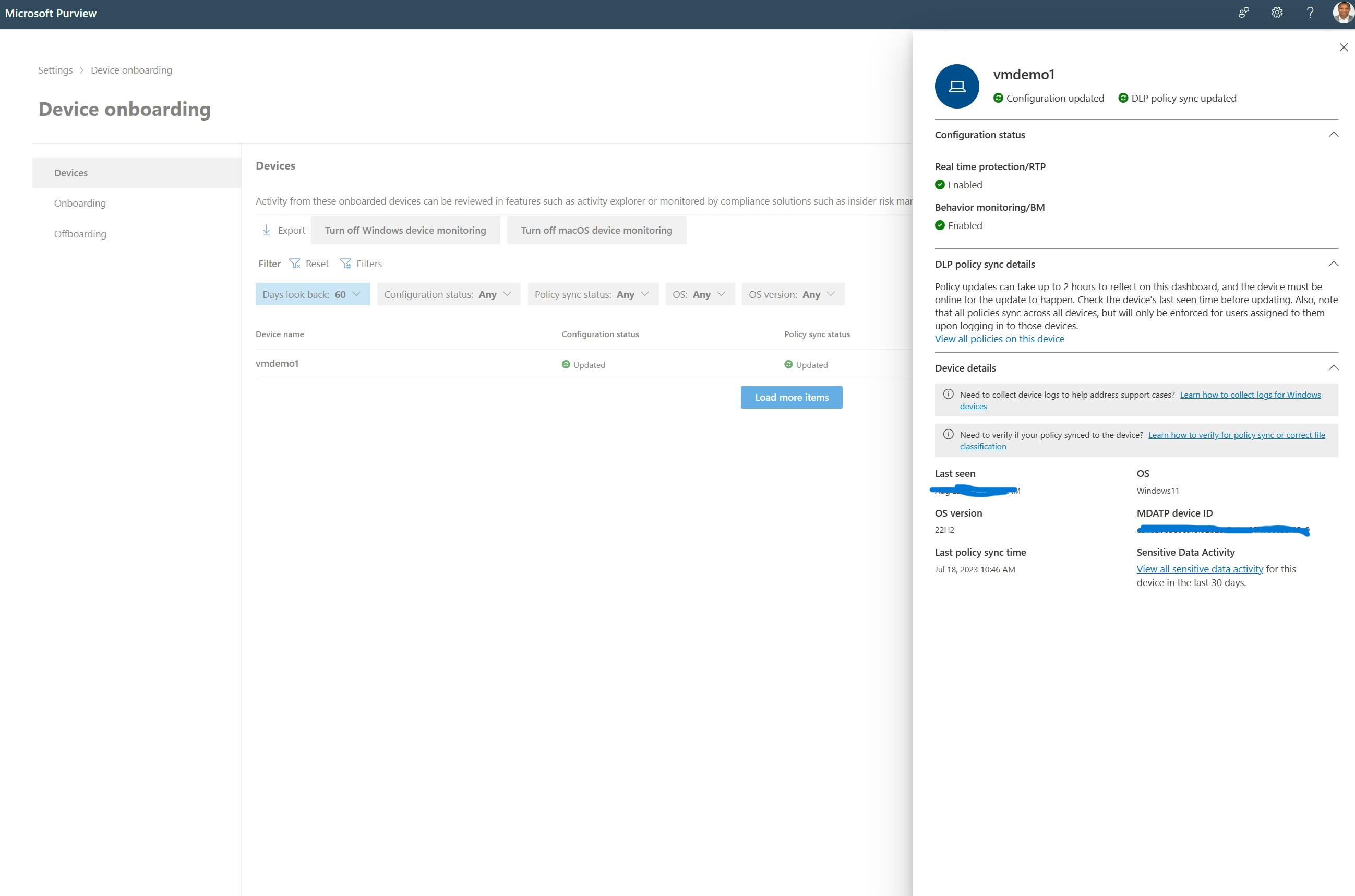
a. Method of onboarding devices to the Purview portal:
Firstly the devices used in the enterprise need to be onboarded into the Purview portal. Example below.
b. Supported browsers where “risky” personal web apps (Dropbox, Google Drive, ChatGPT etc.) can be “grey listed”:
Next, you need to ensure employees are using Edge... or Chrome or Mozilla Firefox if either of those supported browsers have the Microsoft Purview extension installed (you can find it for Chrome here, and for Firefox here). These browsers will be used to monitor corporate file sharing to personal web apps. At Microsoft we generally refer to web apps in this context as service domains.
c. Allowing or blocking web apps in Microsoft Purview’s DLP settings:
Depending on how open your organization is to employees using personal web apps, you may already have a whitelist of service domains (“only these domains allowed”) or a blacklist of service domains (“employees should make their own judgement, but certain domains are off limits”) .
Either way, there can be some service domains that are in the middle. Eg. Allowing an employee to use Dropbox to upload pictures from the company Christmas party that were shared on a corporate Teams channel. But not allowing customer/client IDs or details on SharePoint to be uploaded to that same personal Dropbox storage.
In this case, you want to "greylist" the service domain to prevent certain files from being uploaded. For the DLP policy to work on personal web apps, this greylisting is done in the "settings" section of the DLP solution.
In settings, focus on the service domains of the “risky” storage solutions, for example drive.google.com; or for example chat.openai.com if personal gen AI solutions are also a worry/risk.
There are two flavours to greylisting sensitive data from being leaked.
Allow – this follows the whitelisting logic: if a service domain is not on this list, the DLP policy will trigger, or
Block – this follows the blacklisting logic: if a service domain is on this list, the DLP policy will trigger.
In my example below I've blocked uploads and copy-pasting of sensitive info to 5 popular web apps.
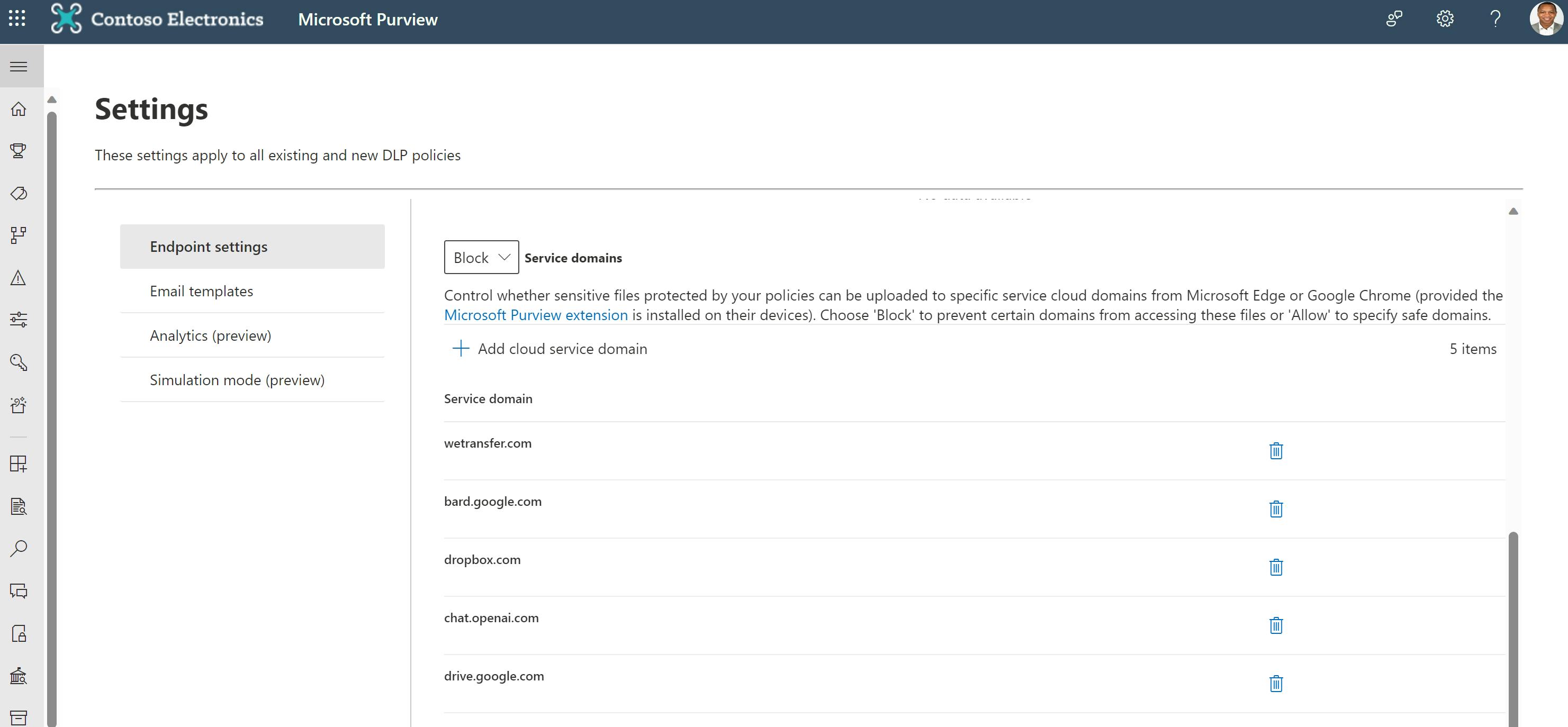
This means users with access to the corporate IT environment can upload/copy sensitive files to any web apps except for the 5 web apps I've greylisted.
I've linked to official Microsoft technical docs on two relevant scenarios, for reference:
Conclusion
Effectively safeguarding corporate data in an era of widespread personal software use requires a focused strategy. By incorporating corporate devices into the Purview compliance portal and enforcing smart data loss prevention policies, you can protect sensitive information while respecting personal boundaries, ensuring a secure yet adaptable digital workspace.
Another question could be about what content you should protect from being uploaded. That's for another elevator conversation, but I cover a few examples here.

